-

The Minimal Phone’s E Ink Screen Will Bore You Out of Doomscrolling
Android14runningonanEInkscreenwithcellularconnectivityandaQWERTYkeyboard?Lifeisnol...
02-21 / 216 Sees / 0 Comment -

The $29 AirTag Killer? This Smart Tracker Has an E-ink Screen for Photos & Contact Information
We’vebeenusingiPodShufflesforsolongthatweforgottheiPodNanoexisted.MeetthePhotoTag–...
02-20 / 427 Sees / 0 Comment -

Could a Remarkable Paper Pro Change How You Organise Your Life?
I’montheMoneyMagpiewritingteam,butI’malsoascreenwriter,developmentproducer,andburgeoni...
02-19 / 492 Sees / 0 Comment -

LG V50 ThinQ Dual Screen phone resurrected as the inkReader Duo e-reader
InspiredbytheLGV50ThinQDualScreenandLGG8XThinQ,theinkReaderDuoisaconceptdevicewit...
02-18 / 499 Sees / 0 Comment -
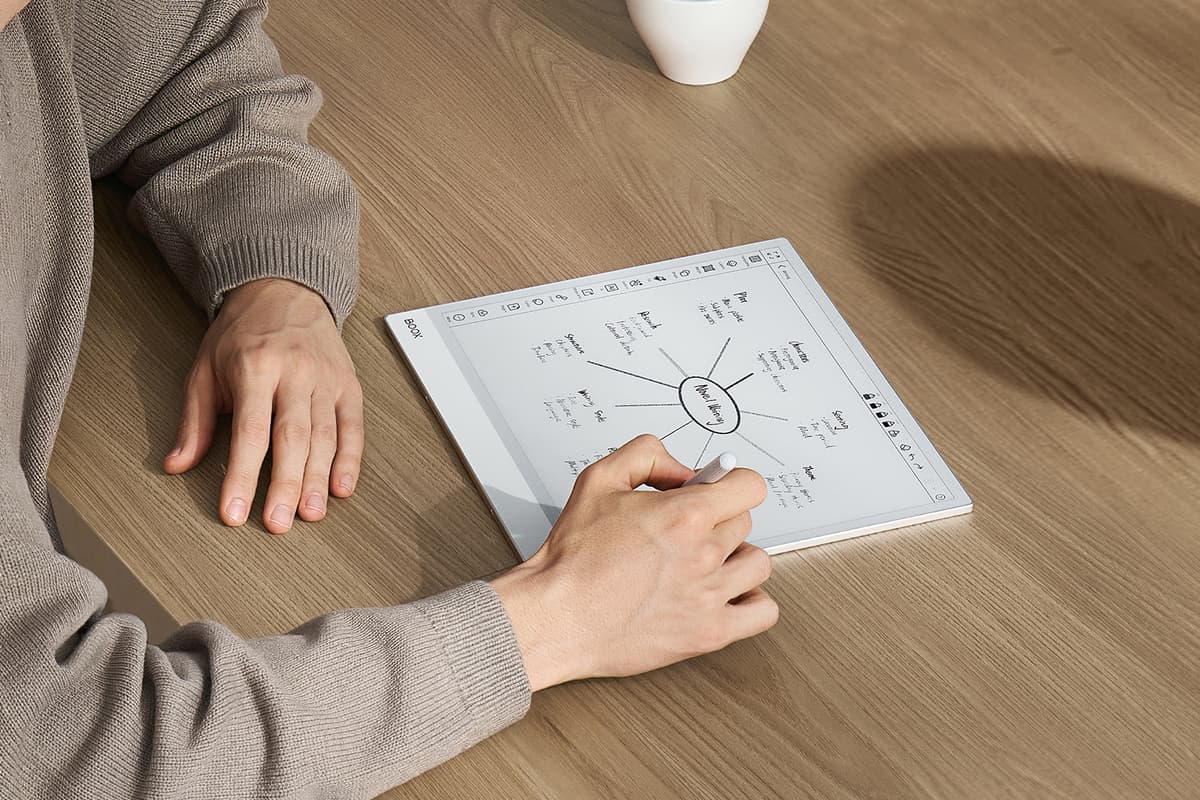
Monochrome e-note grows E Ink productivity to 13 inches
Ifyouliketoscribblethoughtsonpaperbutarelookingforsomethinglesswastefulandmoremoder...
02-17 / 923 Sees / 0 Comment -

Would you pay top dollar for a large E Ink device?
BooxrecentlyannouncedthelaunchoftheNoteMax,a13.3-inchEInktabletthatrunsAndroid,and...
02-14 / 938 Sees / 0 Comment -

Asus' new NUC has a customizable, always-on E-Ink display on top — the army of five NUCs includes ul
Asusjustlauncheditsnext-generationNUCPCs,offeringuserseverythingfrompureperformance,aes...
02-13 / 916 Sees / 0 Comment -

Samsung Unveils Next-Gen Commercial Displays That Operate at 0.00W
SamsungElectronicshasunveileditsnextgenerationofcommercialdisplaysfeaturingAI-poweredsol...
02-13 / 1122 Sees / 0 Comment -

New Hisense A9 Android smartphone features an e-ink display
HisensehasintroducedanewsmartphoneintheA9series.Thismobiledevicecomeswithane-inkdis...
02-12 / 1297 Sees / 0 Comment -

Continental showed an E Ink screen 1.3 meters wide to decorate the car interior
AtCES2025,Continentalunveiledaconceptcarinteriorcalledthe“EmotionalCockpit,”featu...
02-11 / 955 Sees / 0 Comment -

HyRead Gaze Pro X e-Note With 10.3-inch E Ink Carta 1300 Display Launched
HyReadannounceditisallsettolaunchitsall-newe-notedevice,the HyReadGazeProX.The...
02-10 / 1065 Sees / 0 Comment -

ISE 2025 – Lotsa E-Paper, Including Some Big Fellas
Therearenumerouscompaniesbigandsmallishshowingcolore-paperdisplaysatISEthisweek–ever...
02-08 / 1523 Sees / 0 Comment -

E-ink screen performance hits 60 Hz with 10.3-inch portable touchscreen monitor from Dasung
Chinesee-inkmanufacmatchturerDasungjustlaunchedthePaperlike103,a10.3-inche-inkdisplayth...
02-07 / 1393 Sees / 0 Comment -

Wi-Charge now powering E Ink large-format panels
Photo:GeneratedbyAI.AdobeStock.Jan.17,2025Wi-Charge,awirelesselectricityprovider,isnow...
02-06 / 1334 Sees / 0 Comment -

E-Ink Tablets for Note-Taking Professionals
Intheevolvinglandscapeofprofessionaltools,E-Inktabletshaveemergedasindispensabledevices...
02-05 / 1141 Sees / 0 Comment -

SOLUM Debuts Eco-Friendly Full-Color E-signage with E Ink Using E Ink Spectra 6
SOLUM(CEOSung-HoJeon)announcedonthe17ththatitunveiledthenext-generationE-signagefeatur...
02-04 / 1832 Sees / 0 Comment -

New Mateluxue iPhone Case Comes With an E Ink Display, Additional Storage
SeveralcoversfortheiPhonecomewith embeddedEInkdisplays.Soonwearegoingtohaveanot...
02-03 / 1363 Sees / 0 Comment -

Delvaux x E Ink Pin Mini Bucket
“TheEInkPrismmergestraditionaltextileswithinnovativetechnologiesandhasredefinedwhatah...
01-29 / 2284 Sees / 0 Comment -

Pricer launches its latest solution, Pricer Avenue™, to help retailers redefine shelf-edge experienc
Pricer,theleadingin-storeautomationand communicationsolutionsprovider,hasannouncedthe...
01-28 / 2245 Sees / 0 Comment -

SOLUM Showcases Sustainable Retail Innovation at NRF 2025
Koreancompany SOLUM showcasedgroundbreakingretailsolutionsatthe NRF2025 R...
01-27 / 2124 Sees / 0 Comment -

Phone-sized dual-screen E Ink reader concept offers a different way to be productive
E-bookreaderstodaynolongercomeinthedrab,uninspiring,andcheapformsoftheearlyAmazonKi...
01-26 / 2655 Sees / 0 Comment -

You don’t even need to charge this wireless E Ink poster powered by infrared light.
Expandingtheflexibilityofthe rechargeableInkPoster thatdebutedatCES2025,the ...
01-25 / 1994 Sees / 0 Comment -

Asus announced a NUC AI mini PC topped with a color E Ink display.
Calledthe AsusNUC14ProAIPlus,it’sbasically theNUC14ProAI inatranslucent...
01-24 / 2117 Sees / 0 Comment -

This Compact E Ink Phone Promises to Simplify Your Digital Life
Thisyear’sbeenexhausting,hasn’tit?!Especiallythelastfewweekshavebeenemotionallyandmen...
01-23 / 2530 Sees / 0 Comment -

Review: The Supernote Manta is the pinnacle of writing pleasure
FewEInkfandomsareasfaithfulasSupernoteusers. EversincetheNomad (alsoknownas...
01-23 / 2506 Sees / 0 Comment -

5 reasons E Ink displays might be the next big thing for PC setups
It'snosecretthatIloveEInkdevices.I readmostofmybooksonthem, usethemfo...
01-22 / 2607 Sees / 0 Comment -

E Ink to Make a Splash at NRF 2025 With Spectra 6 e-Paper Retail Signage
EInk announced itwillbeshowcasingitsSpectra6full-colorretailsignageattheNRF2...
01-20 / 2177 Sees / 0 Comment -

Continental Low-Energy High-Impact Dashboard Display
Continental,amajorautomotivesupplier,hasunveiledatrulyuniquewayfordriverstopersonalize...
01-20 / 2256 Sees / 0 Comment -

This mammoth Boox E Ink tablet is officially available in the US, UK, and EU starting today
We'veknownaboutBoox'smostrecentlineupofEInktabletsande-readers sinceOctobe...
01-19 / 2664 Sees / 0 Comment -

You only need to charge this E Ink digital poster once a year
EInkhascollaboratedwithPocketBookandSharptocreateanewlow-powerdigitalposterthatdispl...
01-08 / 2930 Sees / 0 Comment -

World's First ePaper Digital Color InkPoster™: the Zero-Watt Future of Displays
LASVEGAS, Jan.7,2025 /PRNewswire/-- Lugano – Meettheworld'sfirst...
01-08 / 4185 Sees / 0 Comment -

Pocketbook InkPoster Announced at CES 2025
PocketbookhasbeenworkingonadigitalInkPosterforalmostayear.TheyhavepartneredwithSharp...
01-08 / 2834 Sees / 0 Comment -

You can customize this Raspberry Pi eInk display with tons of cool plugins
Whenyoupurchasethroughlinksonoursite,wemayearnanaffiliatecommission.Here’showitwork...
01-03 / 4887 Sees / 0 Comment -

Inky Frame: Energy efficient E Ink screen powered by Raspberry Pi
TheInkyFrame7.3isaEInkdisplaycapableofcoloranddesignedforawiderangeofprojectsand...
01-03 / 3181 Sees / 0 Comment -

New Bigme HiBreak Pro E Ink Smartphone Launched
HereissomethingforthoselookingforasmartphonefeaturinganEInkdisplay–theBigmeHiBreak...
01-03 / 3370 Sees / 0 Comment -

Dual Screen E Ink Display Concept Brings Back Slider Phone Format
Smartphonesareundeniablypowerfultools,butthey’realsodouble-edgedswords.Whiletheykeepus...
01-03 / 4648 Sees / 0 Comment -

The reMarkable Paper Pro receives ‘Calm Tech’ certification
Notmanypeoplehaveheardof CalmTechCertication before,butitisbasedoutofNewYor...
12-30 / 3428 Sees / 0 Comment -

Supernote A5 X2 Manta E-Ink Tablet Puts Note-Taking and Reparability at the Forefront
Thecurrentgenerationof note-takingtablets havebecometheperfectreplacementfortrad...
12-27 / 3638 Sees / 0 Comment -

Bigme Hibreak E INK Phone Received Massive Software Update
BigmehastwovariantsoftheirHibreakEINKsmartphone.Onehasatypicalblackandwhitee-paper...
12-26 / 3390 Sees / 0 Comment -

E INK is not just found on e-readers, but all sorts of surprising things
EINKisacompanythatutterlydominatesthee-notebookande-readermarkets.TheAmazonKindle,Ba...
12-25 / 3498 Sees / 0 Comment